Mastering Restaurant Sanitizing: Best Practices for Kitchens and Dining Areas
Master restaurant sanitizing with clear steps for kitchens and dining areas. Learn methods, checklists, and procedures to keep your team safe and...
A food defense plan aims to protect food businesses from intentional product contamination or adulteration.
The globalization of the food industry has opened the system to a vast amount of potential for trade, growth, and food security. Despite this fact, the event has also opened opportunities for unsolicited attacks and acts of terrorism or food defense incidents via the food supply chain.
The U.S. government has taken the initiative to protect the food industry from intentional economic disruption, public health threats, and food fraud.
Under Food Safety Modernization Act compliance, food businesses and processing establishments are required to establish a food defense plan to address any vulnerability in their system against intentional adulteration.
WHAT WE'LL COVER:
Food defense refers to the efforts of the food industry and federal food safety agencies to protect food products from contamination, intentional adulteration, acts of terrorism, and tampering. This regulation is outlined under the Intentional Adulteration Rule of the FSMA.
The threats of food terrorism have been present in the U.S. food industry since early 2000. These threats have caused widespread panic throughout the country, and the initial prompt of the government was to establish the Public Health Security and Bioterrorism Preparedness and Response Act of 2002. This national policy was followed by establishing the Intentional Adulteration Rule (IA Rule) under the FSMA.
Food businesses that satisfy the FDA qualification diagram and requirements must establish a written plan of their food defense strategies in response to the increasing threats of food terrorism. The FDA diagram shows which food businesses reporting under the FDA are required to establish a food defense plan and which businesses are exempted.
Access the FDA flow chart to determine if your food business must create a food defense plan.
The written food defense plan emphasizes strategies on how to protect food and public health from economically motivated threats in the food supply chain. The plan aims to ensure compliance with guidelines for food safety and security as the country's food industry progresses through globalization.
The food defense plan contains comprehensive risk assessments and management systems for food that will protect food businesses and minimize public health concerns.

According to the FSMA 2011 Intentional Adulteration Rule, applicable food businesses must prepare and implement a food defense plan based on a carefully evaluated vulnerability assessment. All food businesses registered under the FDA, except those that qualify for an exemption, must abide by this rule for the protection of food products. 1
As a pioneering government policy, the FDA founded the International Adulteration Subcommittee with the Food Safety Preventive Controls Alliance. The alliance aims to create training resources on food defense practices for food business compliance.
The rule requires all owners, operators, and agents in charge of both domestic and foreign food infrastructures working with the U.S. food industry to comply. Food business owners must create a food defense team that comprises trained personnel and a manager with an adequate understanding of food defense.
The FDA has set compliance dates for food businesses based on the size of the operation.
The U.S. Food and Drug Administration (FDA) created the requirements for creating a food defense plan based on the approach used for Hazard Analysis Critical Control Point (HACCP) system.
The four (4) key components of a food defense plan aim to clearly identify all vulnerabilities and establish appropriate process steps and mitigation strategies or action plans to reduce the risk of intentional adulteration. The FDA outlines the components of a food defense plan example:
The first key component to creating a food defense plan is identifying the most vulnerable points, steps, and procedures in your operations against the risk of adulteration. In assessing vulnerable points, the following factors must be considered:
To facilitate the initial implementation of vulnerability assessments for food businesses, the FDA and other key U.S. food agencies created a partnership program. The primary objective of the program is to validate sector-wide vulnerabilities by conducting on-site physical assessments.
The program is also responsible for collecting information on trends in the food industry and improve mitigation tools.
Some of the most prominent examples of vulnerabilities in a food system include the following:
Mitigation strategies refer to action plans that must be done to protect vulnerable points in your system and ensure that intentional adulteration will not occur. The FDA defines mitigation strategies as risk-based control measures that trained personnel will apply in a food business to reduce the likelihood of an intentional attack on their food products.
Based on the FDA definition of mitigation strategies, plan of action, such as strict security controls, can be established to reduce outside access to a business system. Security can be in the form of physical barriers, zoning restrictions, alarm systems, and limited access by personnel.
The rule states that the established mitigation strategies must be accompanied by a monitoring system.
After the establishment of strategies and action plans, they must be monitored to ensure consistent security against food fraud or intentional adulteration. This component is comprised of three main factors:
All employees involved in protecting food operations through mitigation action plans must receive proper employee training. The regular training program of employees on food defense will strengthen the level of protection in your food business.
In addition, all documents related to food defense must be archived properly in case of review or auditing.
The FDA provides food defense training programs and educational resources to assist first-time implementers of food defense. They also provide food defense audit resources.
Monitoring mitigation strategies is a constant and repetitive task that must be performed every day, or else their purpose will be defeated. Use FoodDocs digital Food Safety Management System to take off the burden of trying to remember to monitor every single strategy in the most intuitive way possible.
Use our free food safety quiz tool to prepare food handlers for more intensive training on food defense.

As the Intentional Adulteration Rule is new legislation, federal agencies provide food defense training and resources to help businesses understand and implement the program better. The FDA, for example, provides Food Defense Training 101.
Training programs for authorized employees on food defense offered by federal food safety agencies consist of courses that will help food business teams understand the importance of a food defense plan. They provide a comprehensive walkthrough of procedures involved in making practical strategies for the safety of food products.
The FDA also offers food defense audit resources for bodies aiming to verify food defense plans and reduce potential health risks.
The intentional contamination events that a food defense program aims to mitigate are a manifestation of a person's motivation, capabilities, and objectives. Threats to the U.S. food supply are not an unknown problem. However, globalization has opened doors for this threat to grow. Food safety statistics show that there is a rise in defense problems, threatening national food security.
Understanding the drivers of food defense incidents can lead food handlers also to understand the reason behind every food defense event.
Food defense intentional contamination events are commonly categorized into three different types:
Food terrorism refers to a food defense incident concerning the deliberate act of contaminating foods to be served to consumers to cause public health harm and affect social, economic, or political events. Terrorism in the food industry has been commonly recorded to be carried out through the addition of chemical, biological, physical, or radiological agents to foods.
The first documented act of food terrorism dates back to 1984. In this event, a group successfully conducted the contamination of salad bars with Salmonella. The act was motivated by the intention of affecting the election, which is considered the largest food attack to date.
Industrial sabotage is an intentional contamination event that involves food handlers either from your food business itself or a competing company. This event is often motivated by the dissatisfaction of a disgruntled employee or intense competition with the intent of causing food safety problems and profit losses for your food business.
An example of this event is if an employee purposefully contaminates frozen foods or raw meat, which will be used as a secondary ingredient for reworking.
The intentional adulteration of food targets to achieve recall in products cause a public uproar and loss of public confidence in food quality and safety. The sabotage does not necessarily need to be fuelled by wanting to cause a widespread health concern.
Economically motivated adulteration is the intentional substitution of a key ingredient or addition of an undeclared substance to increase the value of the product while decreasing the cost of production.
This type of adulteration involves skipping crucial information from the product label. An example is when a food business purposefully substitutes a huge portion of a product with a cheaper ingredient without notifying the public through the product label.
When food manufacturers claim that their products are organic foods, but this is not entirely true, this is considered food fraud. The FDA identifies this type of act as food fraud. Other products that are commonly involved in food fraud include grain-based food, fruit juices, organic foods, meat, and products from poultry establishments. Food fraud also includes diluting functional foods with inactive ingredients, which can also go against allergen labeling requirements.
EMA often does not only involve economic impacts. The substitution can sometimes result in combined health, economic, and psychological impacts.
Understanding the potential drive of an attacker can protect food companies from contamination originating outside the infrastructure and create systems that will protect their products from intentional adulteration.
Motivations by an attacker can be influenced by the desire to cause any or a combination of the following objectives:
Intentional adulteration and other food defense activity types can result from any of these drivers, and the events can overlap in proper categorization. Proper assessment of their objectives can help food business teams address vulnerabilities in their system.

Implementing food defense measures can become more efficient when the developing food business owner understands the vulnerable areas in their food business.
The challenge is identifying the proper sections where these strategies fit to protect products from contamination properly.
The FDA identified four (4) main categories of activity types that require mitigation strategies due to common vulnerabilities:
1. Uniformly mixed products/ batches
Includes products that are homogenized and processed in large batches (e.g., ground meat and baked goods).
Mitigation strategies for this category include:
2. Large batch size
Includes food service and food production operations that produce foods in large volumes.
Mitigation strategies may include:
3. Short shelf life products
Includes perishable food items, such as milk and dairy products.
4. Easily accessible entry points
Includes backdoors, loading points, entrances, and other obvious entry points.
Food safety analysts have come up with a list highlighting the main principles needed to succeed in a food defense program. Food handlers can be guided in establishing and the adoption of food defense by following these proactive key activities:
The listed important elements of a food defense plan emphasize a proactive approach similar to what the FSMA promotes. The idea is to prepare food businesses against potential attacks of intentional adulteration and become ready to address any case.
As one of the main food safety agencies in the U.S., the U.S. Department of Agriculture Food Safety and Inspection Service (USDA FSIS) focuses on working with other government agencies, the food industry, and private industry partners to create new plans and strategies to suppress potential intentional adulteration incidents. The FSIS creates tools, references, and systems that will encourage food businesses to adopt a functional food defense plan.
A functional food defense plan is a program that suffices the following criteria:
The FSIS Significant Incident Preparedness and Response Staff (SIPRS) works closely with food businesses on how to identify vulnerabilities and establish defense strategies to reduce health risks. The food safety agency focuses on national policies and law enforcement and guiding food businesses through the implementation of food defense practices. Their initial target was to establish a functional food defense plan in 90 percent of establishments by 2015.
Food defense and food safety are terminologies used to identify practices for food safety and policies that aim to control issues that may cause public health harm through the food they consume. They are both key factors in the food protection risk matrix.
Food defense focuses on controlling intentional adulteration incidents by ill-motivated individuals, whereas food safety focuses on unintentional contamination of food product contents. Where food safety focuses on properly handling leftovers with care or cooking raw meats to a safe temperature, food defense focuses on keeping potential attackers from sabotaging the process. Both systems aim for the safety of food from contamination.
Achieving control over the defense and understanding why food safety is important contributes to food security, which is the ability of a nation to provide safe food for people at all times and allow people to meet their dietary needs and maintain an active and healthy life.
Another factor that contributes to lessening the potential of an intentional adulteration attack from a disgruntled employee is strengthening the food safety culture. When all employees understand the importance of their work and the overall ideals and values of the whole team are unified, the chances of an ill-motivated employee causing economic sabotage are lessened.
Learn about the essential rules and tips for food safety from our blog articles.
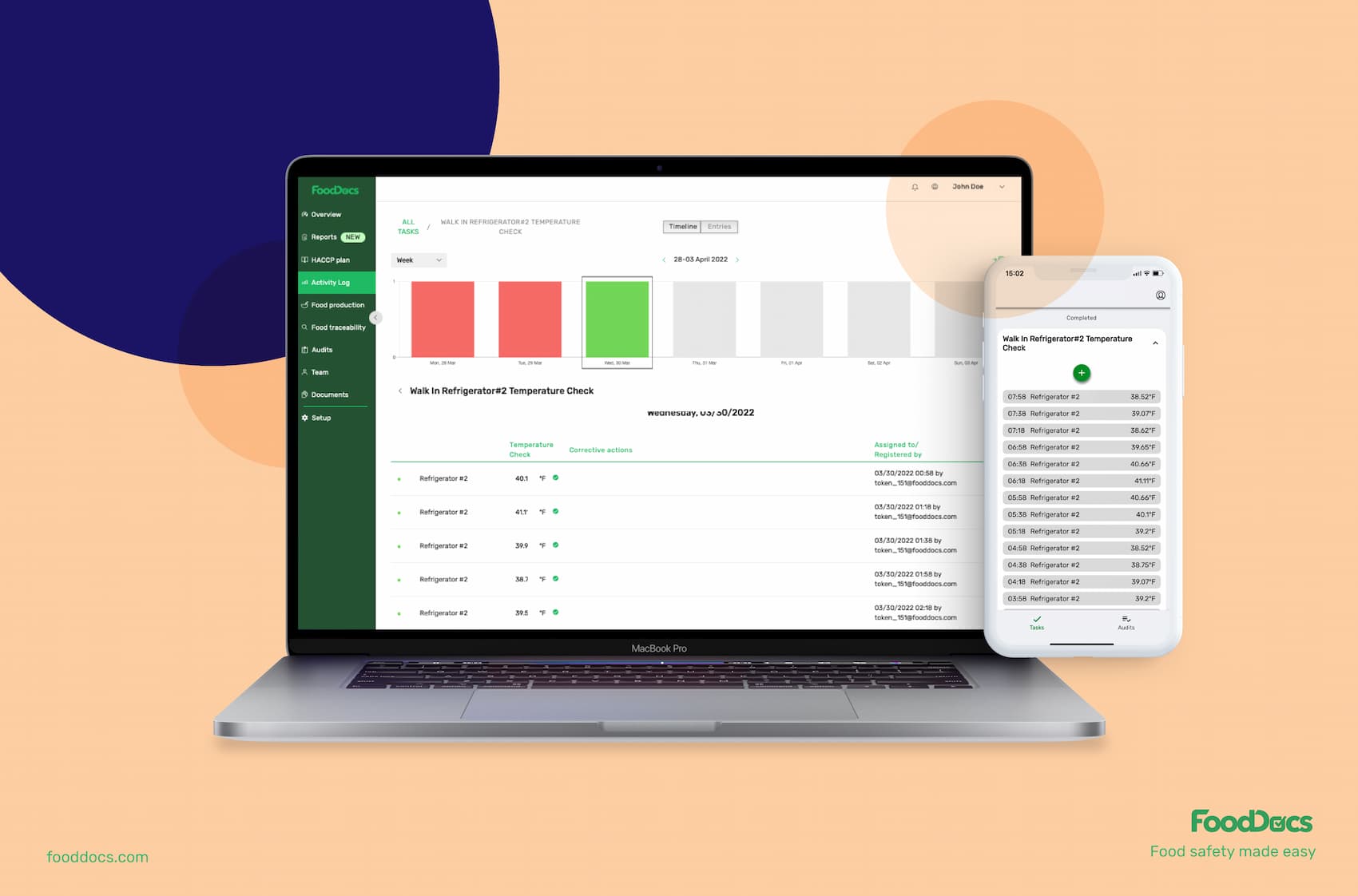
A key element to ensuring that mitigation strategies are strictly followed is through implementing a comprehensive monitoring system. Consistent monitoring is a key method to prevent poor food safety and can give your team the needed insight to determine if the strategies are working, if your food product contents comply with standards for food safety, and if your business is compliant with government policies.
All vulnerable points and areas in your food businesses must be overseen, and as the food business owner or food safety manager, it is part of your responsibility to understand and assess the current atmosphere of your business.
Highlighting the importance of food safety and combining the efficiency of artificial intelligence technology is FoodDocs' digital Food Safety Management System.
This digital solution can help food handlers remotely and intuitively monitor mitigation strategies through the following features and benefits:
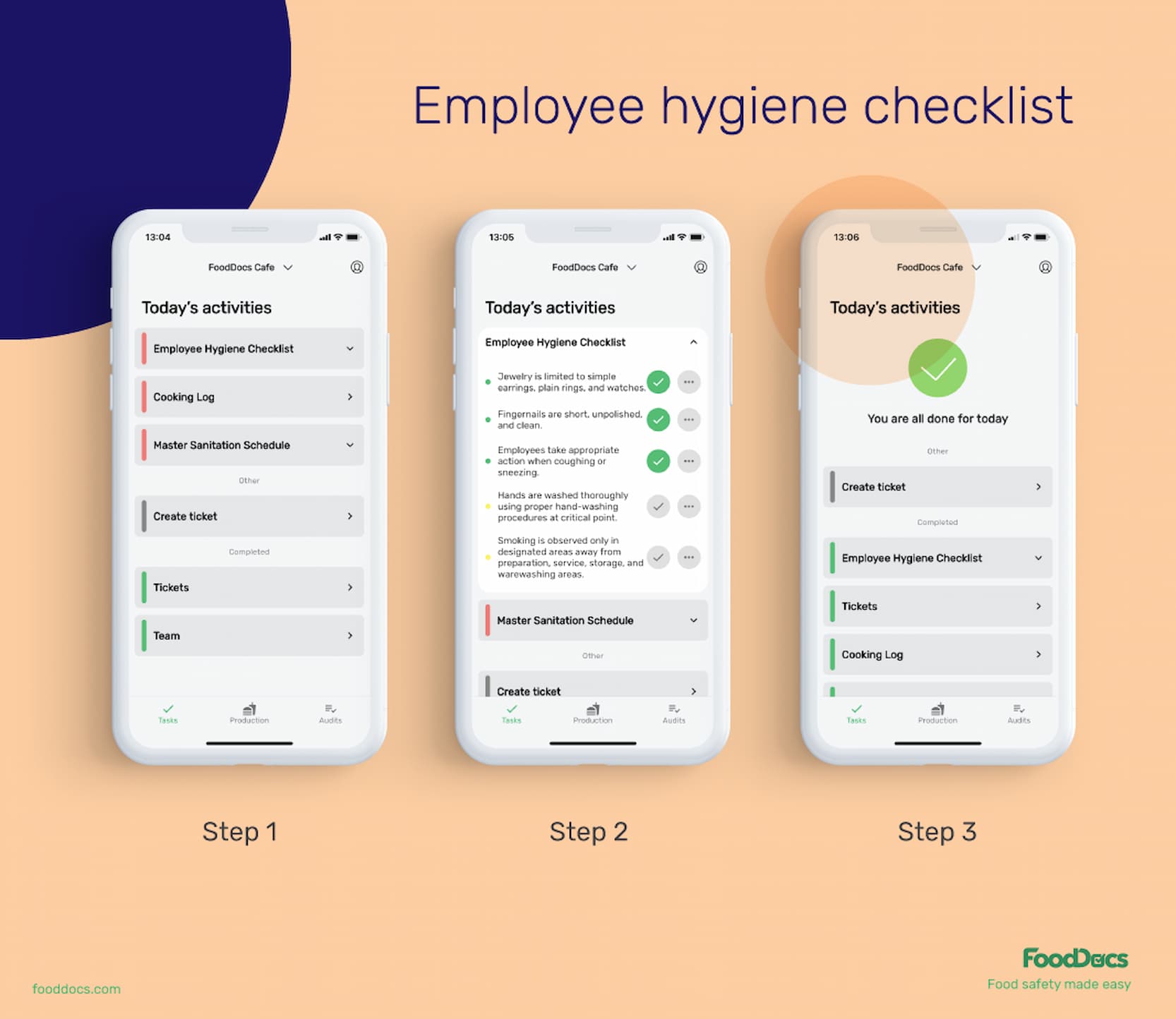
In addition to features that will help improve efficiency in monitoring mitigation strategies, FoodDocs' digital Food Safety Management System also provides features that will help managers control operations.
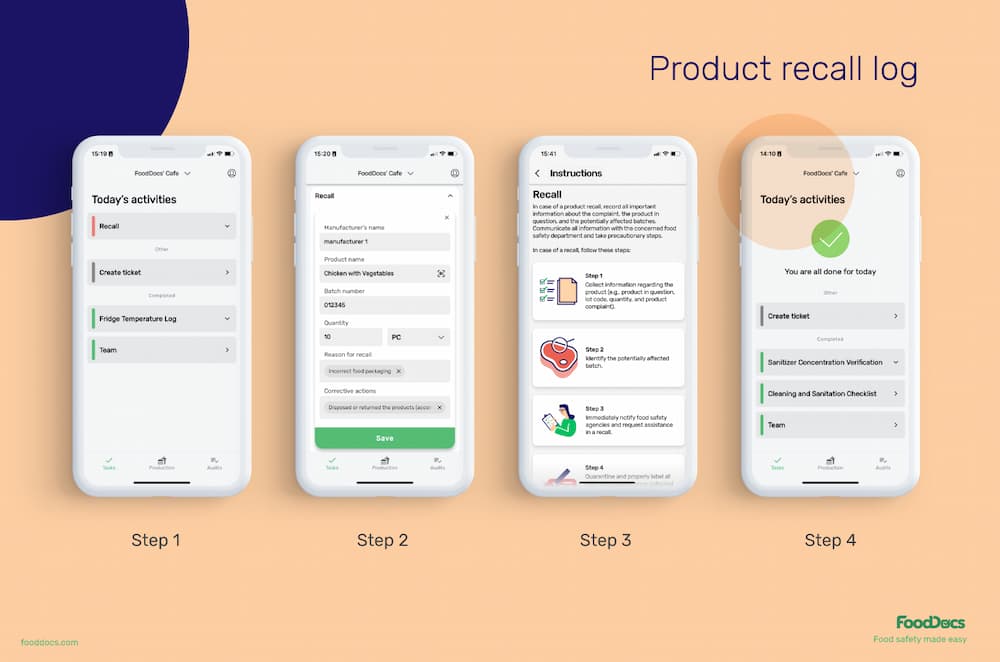
Setting up this digital monitoring system is as easy as describing your operations to our system. All you need to do is answer a few basic questions about your operations, and the monitoring system can be implemented within just 15 minutes.
What's even more useful is you can create your own mitigation strategy monitoring logs or customize existing logs anytime you want.
If you want to experience these features and start securing your team from potential attacks, you can try our services for free using our 14-day trial.
Here are some of the most frequently asked questions regarding the food defense plan under the Intentional Adulteration Rule.
The food defense program is a system established by the FDA under the FSMA law, which consists of steps that will help food businesses protect their food from acts of intentional contamination and adulteration.
Food defense refers to the protection of food products and operations from intentional contamination or adulteration that can cause public health concerns or economic problems in the food supply chain.
On the one hand, food safety refers to the practices that help prevent unintentional contamination in the supply chain. On the other hand, food defense focuses on intentional attacks that lead to the contamination or adulteration of food products.
The food defense program highlights activities that are most vulnerable to intentional contamination:
Food defense definition refers to the program that prevents intentional adulteration and contamination of food products, whereas food fraud is a type of food defense event that is economically motivated. The difference between food fraud and food defense is highlighted by the fact that food defense is an inclusive term used to prevent events such as food fraud.
Vulnerability assessment refers to the activity of identifying, quantifying, and ranking vulnerable points in a food business' system against intentional adulteration. This step is a prerequisite for establishing mitigation strategies that will protect your food business from any motivated attack and is a core element in the adoption of food defense.
Master restaurant sanitizing with clear steps for kitchens and dining areas. Learn methods, checklists, and procedures to keep your team safe and...
Learn challenges healthcare foodservice teams face today and key food safety practices to protect vulnerable patients. Get a free healthcare leader...
Learn what Standard Operating Procedures (SOPs) are and how to write effective SOPs that ensure consistency, efficiency, and safety in your...